Getting Started
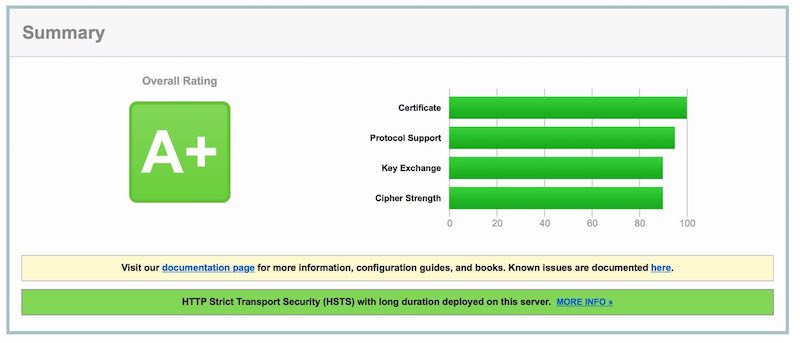
I currently running this site along with several others using Digital Ocean or Vultr combined with Ubuntu 16.04 LTS and Nginx as a websever hosting applications from Discourse to WordPress. Using Qualys SSL Labs tester I initially got a ‘B’. That was on a machine configured with Let’s Encrypt using EasyEngine on default settings. After making minor changes, as shown below, I received an ‘A’, but I will show how you can receive an ‘A+’.
Using Let’s Encrypt with default settings means the SSL/TLS configuration will be in /etc/nginx/nginx.conf. While the settings below, may get you a good score, please be aware that you will disable support for many older browser and devices. If you want to read more about this I suggest checking out: Mozilla Wiki - Server Side TLS and Mozilla Configuration Generator
##
# SSL Settings - Grade: 'A'
##
ssl_session_cache shared:SSL:20m;
ssl_session_timeout 10m;
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256';
ssl_prefer_server_ciphers on;
ssl_protocols TLSv1.2;
Cipers and Protocols:
Generate stronger Diffie-Hellman Key:
cd /etc/ssl/certs
openssl dhparam -out dhparam.pem 4096
Update Nginx configuration:
##
# SSL Settings
##
ssl_session_cache shared:SSL:20m;
ssl_session_timeout 10m;
ssl_ciphers 'ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-ECDSA-DES-CBC3-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA:!DSS';
ssl_prefer_server_ciphers on;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_dhparam /etc/ssl/certs/dhparam.pem;
ssl_stapling on;
ssl_stapling_verify on;
resolver 208.67.222.222 208.67.220.220 valid=300s;
resolver_timeout 5s;
OSCP Stapling and HSTS:
Please note that enabling HSTS means that any browser accessing your site will be instructed to make all connections over SSL/TLS for the next 6 months. This means you must ensure you are comfortable maintaining TLS (certificate updates, etc.) because clients browser default after encountering HSTS will not allow for easy transition to insecure. You also must be absolutely sure that all resources are loaded securely, otherwise they will simply fail to load for users.
sudo nano /etc/nginx/sites-available/example.com
Add the following parameters after the other ssl configuration lines:
ssl_trusted_certificate /etc/letsencrypt/live/example.com/chain.pem;
# HSTS (ngx_http_headers_module is required) (15768000 seconds = 6 months)
add_header Strict-Transport-Security max-age=15768000;
Restart Nginx: service nginx restart
Now try retesting your site and you should see an A+ rating!